Occasional witterings…
23 Jan 2015
Three of us from LDC Via are at ConnectED this week: Ben Poole, Mark Myers (@stickfight) and Julian Woodward (@woowar). We will have LDC Via leaflets to give you, and the crossword and clues are on the back. Do it to the best of your ability (some of the clues are bastard hard - at least we hope so) and hand it back to us by the deadline. Simple. Remember: you could win a Sonos Play:1.
Competition rules, for the avoidance of stress and fisticuffs
- Only those physically present at the ConnectED conference venue are eligible for the prize.
- You do not have to be a registered conference attendee to be eligible for the prize.
- Your completed crossword must be returned to us by midday on Wednesday 28th January.
- The prize winner will be drawn at random from the fully-correct submitted crosswords.
- In the event of no fully-correct answers, the prize will go to the person (or be drawn at random from the persons) with the most correct answers.
- If you are a registered conference attendee, and you cannot locate Ben, Mark or Julian in time, you may email a scan/photo of your completed sheet, by midday on Wednesday, to [email protected]. (Please make sure it’s legible).
- The prize will be awarded at the Closing Session on Wednesday afternoon.
- If the winner is not at the Closing Session, the prize will be shipped directly to them after the conference.
If you are not at the conference, but fancy having a go anyway (or you are at the conference but want to make a head start) here is the full crossword with clues. We will post a completed version after the conference and you can see how well you did.
22 Jan 2015
We were scratching our heads and twirling our moustaches at LDC Via Towers, wondering what we could do as a bit of fun for ConnectED next week.
And then the penny dropped: what could be more “ConnectED” than … a competition crossword?! At what seems (no official word, but we all know it is don’t we?) to be our last January visit to the Swan & Dolphin, and possibly (perhaps IBM will tell us next week) the last conference recognisable as the “Lotusphere” we know and love, we decided to create a little bit of fun to fill in the dull moments (as if!) and test your knowledge of Lotus, Lotusphere and IBM. And, yes, we’re freely using the ‘L’ word, without embarrassment, because this is an unashamedly nostalgic effort, looking back affectionately on our collective journey down the years with the softwareformerlyknownasLotusNotes and its stablemates from Lotus and IBM.
You may have noticed that this is a ‘competition’ crossword. Yes, there will be a prize: a Sonos Play:1. If you’re not a Sonos user already, you will love it. And if you are a Sonos user already, you will love it.
In the next post we’ll outline the rules for the competition, and reveal the crossword itself.
21 Jan 2015
We’ve talked previously about integrating LDC Via with XPages but the whole point of our REST API is that anything that can talk over a network can use our services. So we’ve been busy.
So far, when you access the LDC Via website, you get some pre-rolled templates that allow you to view your old Domino data in an easier to read way. We provide templates that work with your migrated Mail Files, Discussions, Document Libraries and Teamrooms. But how about creating your own custom applications?
Today we have released our first public template. It’s a standalone implementation of the classic Teamroom that has been created using AngularJS.
First things first, you can go and play with the template here the username is [email protected] and the password is Password00.
This is not meant to be a masterpiece of UI design, or even the most full featured Teamroom clone in history. But what it does show is an existing Teamroom database that was migrated to LDC Via using our tools and then allows you to continue using it, adding new documents and responses. All of this is done using static HTML and Javascript pages that talk to the LDC Via REST API using standard AngularJS functionality. Indeed, the app we’ve linked to is running on a boring old web server with no fancy schmancy authentication engines or server side scripting.
What this means is that you can create and deploy quite complex business applications with nothing more than a simple HTTP server, LDC Via takes care of everything else for you including data storage and authentication.
We’ve made the source code for the template available for use from Github under the MIT license, so you will be able to make use of the code to get going with your own custom applications.
20 Jan 2015
Mark, Julian and Ben will all be at IBM ConnectED from Friday evening this week. If you’d like to say hello, talk about LDC Via, enter our competition (come back in a couple of days to find out about that) or simply share a beer / some ludicrous sugary confection (in the case of the Wookiee), we’d be delighted to see you.
As you probably know, the conference itself is taking place in the Swan this year. Mark will be around a lot, although staying off-site, whilst the other two reprobates are also residing in the Swan, so will no doubt be irritatingly easy to find.
In addition to general lingering and chatting, you will be able to find Mark at his splendidly useful “Beyond The Every Day” session, “1 App, 2 Developers, 3 Servers: Getting the Same Application to Run on Different Servers” which is happening at 3.45pm in Mockingbird 1 - 2 on Tuesday—here’s a session link for those with ConnectED site access: https://portal.ibmeventconnect.com/wps/myportal/connected/site/Sessions/SessionFinder/detail/00071
Additionally, Mark has somehow become an IBM Champion (no we don’t know how either), and as such you will be able to find him at the Leadership Alliance events looking out of place and desperate to talk tech with anyone.
If you need to know what we look like (oof), take a look-see here. Smooth.
(For those wondering why Matt is not with us this week… he claims to have a very good reason, but we’re unconvinced ;-))
08 Dec 2014
One of the key use cases for LDC Via that we see is for archiving data for successful IBM Domino applications. We all know that Domino has limitations: when a database gets too big, it can really affect performance… but there’s so much good stuff in Domino–like security and integration with email–that it would be a shame to have to migrate your whole application to a completely different platform.
What if there was a “middle ground”? How about moving older or inactive data to a different storage area, but one that still maintains document-level security? You may be surprised to learn how straightforward it is to integrate XPages with other platforms via a REST API.
By way of illustration, we’ve created a sample Domino application that connects to the LDC Via service, obtains a list of LDC Via-supplied databases that the current user can see, and lets the user browse those databases (an individual MongoDB database contains one or more “collections”, and each collection contains documents). Hopefully you can see by looking at the code that makes up the sample app just how easy this is. The main component that drives it all is a managed bean that pulls data from our REST services:
Using this code combined with a single XPage, we can retrieve the aforementioned database list, together with lists of collections within those databases, and for each collection the documents it contains (all based on what the user is permitted to see):
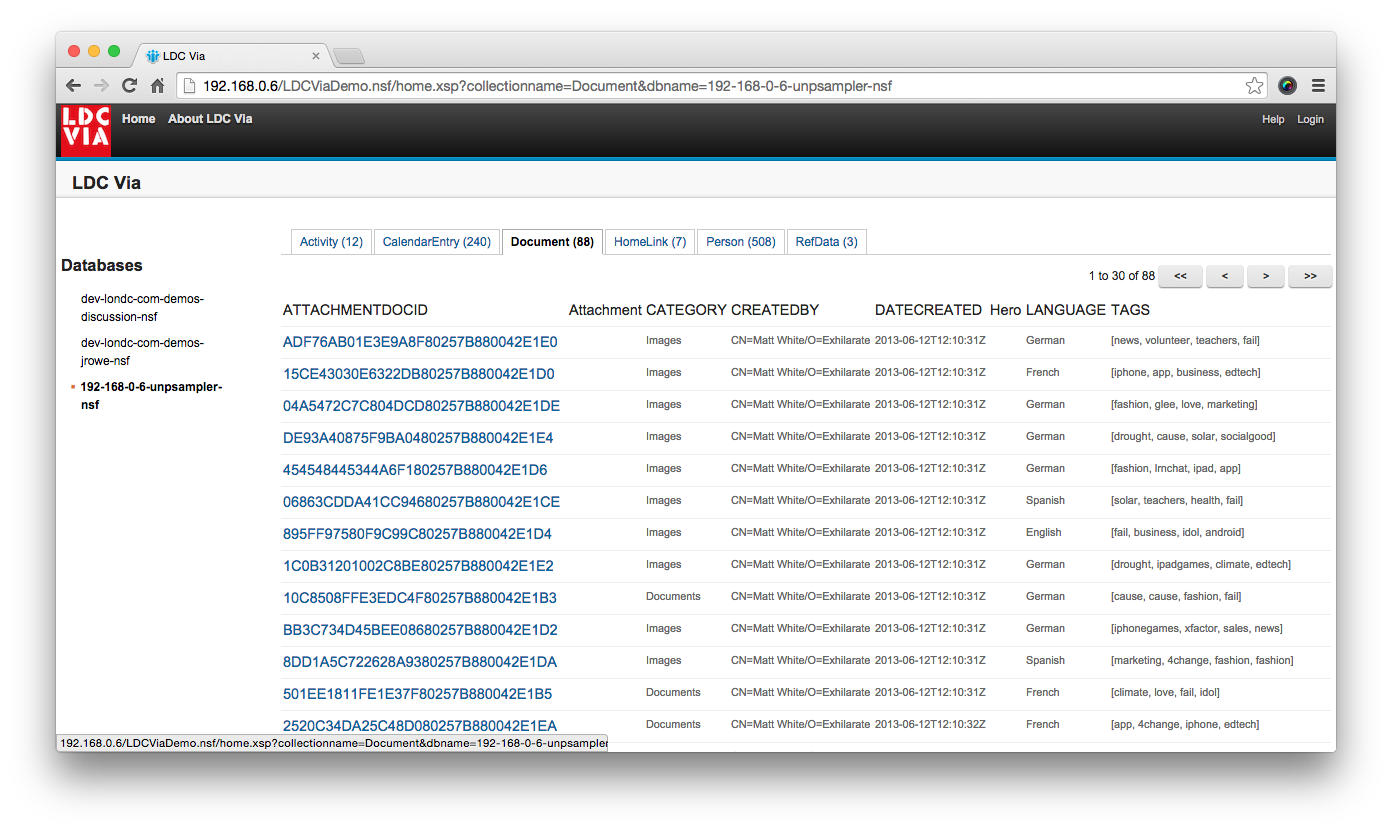
The screenshot shows the list of migrated NSF files (“databases”) that our test user has access to. We’ve selected the database called unpsampler.nsf, and then a collection therein called “Document”. This collection contains 88 documents accessible to the user, and using the API we can then view the first 30 documents, paging through the rest in much the same way you would with a Domino view.
This is a very simple demo, and it wouldn’t take much effort to customise the code to fit your specific requirements. From the end user’s point of view there need be no difference at all in their experience, except that your XPages application is hopefully more responsive as you reduce the amount of live data you’re working with!

